
contractor for the Department of Defense?
If you are a company that has (or wishes to have) a contract with the U.S. government or the Department of Defense, you have probably come to realize that achieving and maintaining cybersecurity compliance is a requirement you can’t afford to neglect.
 Contractors – both primes and subs – in the federal supply chain are responsible for protecting the security of the controlled unclassified information (CUI) they access, create, transmit, or touch while working for the government. To even have the opportunity to bid on contracts, they have to prove that they’ve met the requirements laid out in NIST SP 800-171.
Contractors – both primes and subs – in the federal supply chain are responsible for protecting the security of the controlled unclassified information (CUI) they access, create, transmit, or touch while working for the government. To even have the opportunity to bid on contracts, they have to prove that they’ve met the requirements laid out in NIST SP 800-171.
The purpose is clear—protecting sensitive information is critical for national security. But the bottom line is even clearer—if you don’t meet NIST and DFARS requirements, your contracts and your ability to bid on future work are on the line.
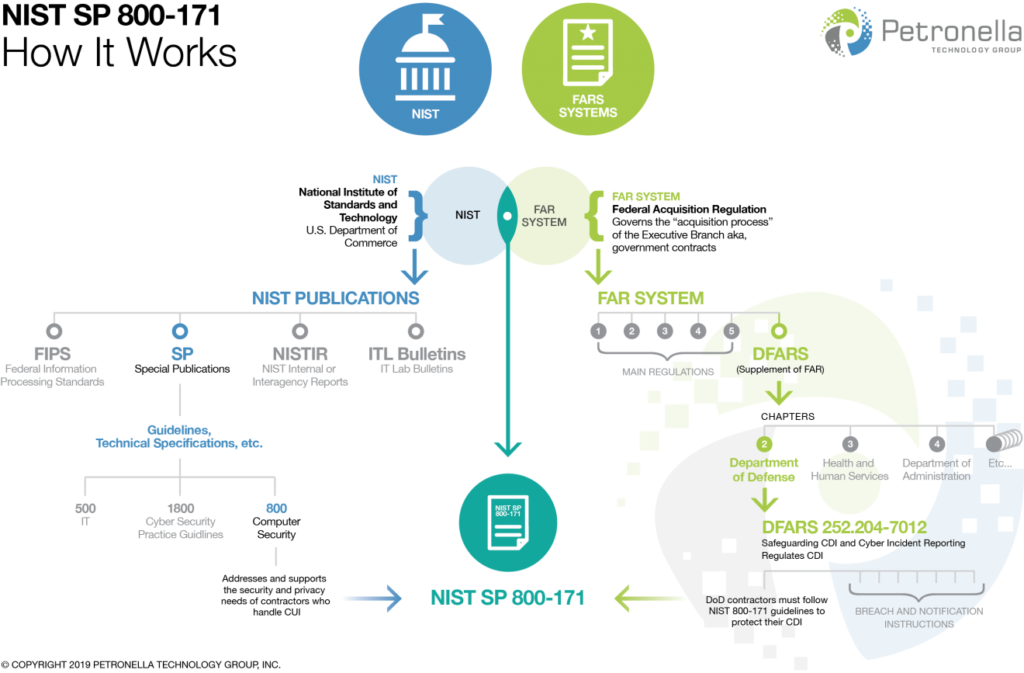
Understanding NIST SP 800-171
The National Institute of Standards and Technology (NIST) is a nonregulatory federal agency tasked with “promot[ing] U.S. innovation and industrial competitiveness by advancing measurement science, standards, and technology in ways that enhance economic security and improve our quality of life.” Their mission includes developing and publishing security compliance standards for the federal government and any organization that handles government data.
NIST Special Publication 800-171, titled “Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations” was originally created in 2015. It outlines the cybersecurity guidelines for contractors who handle CUI.
Under Defense Federal Acquisition Regulation Supplement (DFARS) 254.204-7012, contractors were mandated to apply the guidance outlined in NIST 800-171 to covered defense information (CDI) as well.
Meeting these standards isn’t a theoretical requirement—as of December 1, 2020, every DoD prime, sub, and vendor has been required to upload an assessment onto the Supplier Performance Risk System (SPRS) to even be considered for a contract.
What NIST SP 800-171 Mandates
NIST SP 800-171 is made up of 110 different security controls, broken into 14 separate families. These can be grouped into four main categories:
- Controls: Regulate who can and can’t access CUI and how the data is handled.
- Monitoring & Management: Covers how you monitor the CUI that you handle and how you manage your data and processes.
- End User Practices: Refers to the steps you take to reduce the risk of user errors that can compromise security.
- Security Measures: Encompasses the steps (such as secure backups and firewalls) that we typically associate with cybersecurity.
Chances are, if your organization takes cybersecurity seriously at all (and you should!), you already meet a large number of the controls outlined in NIST SP 800-171. Better yet, the work you do to get in compliance will pay off in better cybersecurity in general for your organization.
The question is: Do you even know where to start in figuring out what needs to be done?
That’s where Petronella Technology Group (PTG) comes in! We can help you determine where you’re at now and what steps you need to take to become fully compliant.
With our FREE self-assessment you’ll get a clear view of where you currently stand. There’s no need to feel overwhelmed or confused—PTG can help you implement NIST 800-171 to keep your CUI (and your contracts!) safe and secure. Take our assessment or get started with a free initial consultation here.






